Free ethereum Spinner – A Honey Trap
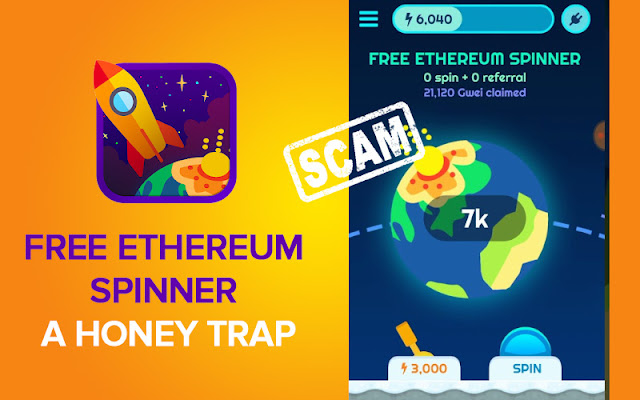
All work and No Play makes Jack a dull boy’. Since childhood we have been taught to maintain a balance between the work and recreation to revitalize the mind’s abilities. Online gaming is gaining immense popularity especially among young generation as it is a source of entertainment and refreshment after a hectic schedule. Earning money by playing games online at the same time would be the icing on the cake. Most of us may be acquainted with the fact that earning money by playing games online is now possible. However earning a quick buck without spending a penny is like dream come true. With Free Ethereum Spinner and similar cryptocurrency game apps available on Google Play Store, you can mint money while enjoying playing. All you need is an android phone and access to Internet. Excited ? Don’t Be! Read more! Free Ethereum Spinner is an android application available on Google Play Store from February 2018. The app has been well received by the public with more than 100,0







